提醒:本文最后更新于 3083 天前,文中所描述的信息可能已发生改变,请仔细核实。

最近一些博友反馈说收不到我博邮件,经过检查,发现少许邮箱出现了,如下所示回馈:
mail server rejected a message that claimed an envelope sender address of kn007.net
it was rejected by the server for the recipient domain mta-189.21cn.com为此,我专门为VPS的DNS解析,添加了如下所示的SPF信息:
v=spf1 a mx mx:kn007.net ip4:50.2.54.2 ~allMX记录:
kn007.net.default._domainkey记录TXT的DKIM协议:
v=DKIM1; g=*; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDPY9DY0gk18N7osVZA6JzLoUzUuP7Q6s5DJyfGVKJUGxxwhg2WXY3jBN/McJdNg+jyUOr7+XVm9+VguJSZDfzCsCHJOei0fTUpW7Xi4xRJaGMoIMiV1wovBHDSTk55xX4ihuMHZcLKVGALuQtK+skeHEEvDE4nxaktNvTS2MaXnQIDAQAB最后为postfix添加了DKIM协议,具体DKIM安装,有些麻烦,反正我是用wget来build安装没成功,估计是没搞site.config.m4或者define的不对。
提供另外一种安装方式,原创(保留了之前错误的尝试,以#注释):
rpm -ivh http://download4.fedora.redhat.com/pub/epel/5/`uname -i`/dkim-milter-2.8.3-8.el5.`uname -i`.rpm --nodeps
wget -O dkim-milter.tar.gz http://sourceforge.net/projects/dkim-milter/files/latest/download?source=files
#wget -O dk-milter.tar.gz http://sourceforge.net/projects/dk-milter/files/latest/download
tar zxvf dkim-milter.tar.gz
#tar zxvf dk-milter.tar.gz
cd dkim-milter-*
#ln -s ../dk-milter-*/libdk
#cp site.config.m4.dist site.config.m4
#echo "define(`confMANROOT', `/usr/share/man/man')" >> site.config.m4
#cp ./site.config.m4 devtools/Site/site.config.m4
#./Build
#./Build install
mkdir -p /etc/dkim-milter/keys/
cp ./dkim-filter/dkim-genkey.sh /etc/dkim-milter/keys/
cd /etc/dkim-milter/keys/
chmod +x ./dkim-genkey.sh
chown dkim-milter /etc/dkim-milter
chmod 700 /etc/dkim-milter
chgrp postfix /var/run/dkim-milter
chmod 770 /var/run/dkim-milter
./dkim-genkey.sh -r -d `hostname -f`
chown dkim-milter /etc/dkim-milter/keys/default.private
mv /etc/dkim-milter/keys/default.private /etc/dkim-milter/keys/default.key.pem
#会生成default.txt 和 default.private
#根据default.txt 里面的内容,将DNS的TXT记录添加好
#default.private已安置好,并改名为default.key.pem,可以使用了
#下面的命令,大家根据实际微调
echo "*@kn007.net:kn007.net:/etc/dkim-milter/keys/default.key.pem" >> /etc/mail/dkim-milter/keys/keylist
echo 'USER="dkim-milter"' >> /etc/sysconfig/dkim-milter
echo 'PORT=local:/var/run/dkim-milter/dkim.sock' >> /etc/sysconfig/dkim-milter
echo 'SELECTOR_NAME="default"' >> /etc/sysconfig/dkim-milter
echo 'SIGNING_DOMAIN="kn007.net"' >> /etc/sysconfig/dkim-milter
echo 'KEYFILE="/etc/dkim-milter/keys/default.key.pem"' >> /etc/sysconfig/dkim-milter
echo 'SIGNER=yes' >> /etc/sysconfig/dkim-milter
echo 'VERIFIER=yes' >> /etc/sysconfig/dkim-milter
echo 'CANON=simple' >> /etc/sysconfig/dkim-milter
echo 'SIGALG=rsa-sha256' >> /etc/sysconfig/dkim-milter
echo 'REJECTION="bad=r,dns=t,int=t,no=a,miss=r"' >> /etc/sysconfig/dkim-milter
echo 'EXTRA_ARGS="-h -l -D"' >> /etc/sysconfig/dkim-milter
echo 'Canonicalization simple' >> /etc/mail/dkim-milter/dkim-filter.conf
echo 'AutoRestart yes' >> /etc/mail/dkim-milter/dkim-filter.conf
echo 'AutoRestartRate 10/1h' >> /etc/mail/dkim-milter/dkim-filter.conf
echo 'Domain kn007.net' >> /etc/mail/dkim-milter/dkim-filter.conf
echo 'SubDomains yes' >> /etc/mail/dkim-milter/dkim-filter.conf
echo 'Selector default' >> /etc/mail/dkim-milter/dkim-filter.conf
echo 'MTA MSA' >> /etc/mail/dkim-milter/dkim-filter.conf
echo 'KeyFile /etc/dkim-milter/keys/default.key.pem' >> /etc/mail/dkim-milter/dkim-filter.conf
echo 'Background yes' >> /etc/mail/dkim-milter/dkim-filter.conf
echo 'Socket local:/var/run/dkim-milter/dkim.sock' >> /etc/mail/dkim-milter/dkim-filter.conf
echo 'X-Header yes' >> /etc/mail/dkim-milter/dkim-filter.conf
echo 'LogWhy yes' >> /etc/mail/dkim-milter/dkim-filter.conf
echo 'Userid dkim-milter' >> /etc/mail/dkim-milter/dkim-filter.conf
echo 'SignatureAlgorithm rsa-sha256' >> /etc/mail/dkim-milter/dkim-filter.conf
echo 'smtpd_milters = local:/var/run/dkim-milter/dkim.sock' >> /etc/postfix/main.cf
echo 'non_smtpd_milters = local:/var/run/dkim-milter/dkim.sock' >> /etc/postfix/main.cf
echo 'milter_protocol = 2' >> /etc/postfix/main.cf
echo 'milter_default_action = accept' >> /etc/postfix/main.cf
chkconfig --level 345 dkim-milter on
service dkim-milter start
service postfix reload
#有bug或者一些错误,欢迎交流!
以上安装方式适用于centos。
目前已有DNS解析:
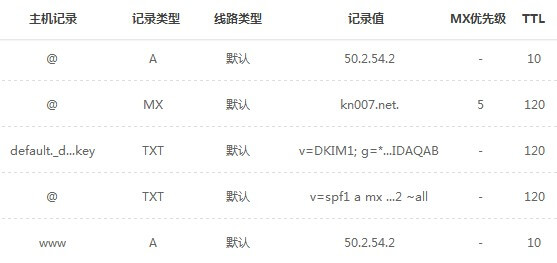
有几个测试网站,测试后的结果都是没问题了:
http://www.openspf.org/Why?show-form=1
The domain kn007.net has authorized 50.2.54.2 to send mail on its behalf, so the message should have been accepted. It is impossible for us to say why it was rejected.http://dkimcore.org/c/keycheck
This is a valid DKIM key recordhttp://www.brandonchecketts.com/emailtest.php
As long as your score is below 5, you shouldn't run into any serious delivery issues.这样完成后DKIM到底有没有作用,我也不晓得,因为我发出的邮件还是没带DKIM签名,或许这个问题需要高手来解答下。
转载请注明转自:kn007的个人博客的《Postfix添加DKIM协议,完善DNS中的SPF解析》

好复杂。。
@Arch!Tech: 也不是很复杂,最后发现SPF是生效的。但是DKIM由于托管商不支持而告一段落。。
一直搞不懂这个有啥用 也不会设置 评论回复通知就看见用163域名邮箱的会出现错误
@空空裤兜: 出现错误?这个是一种验证方法,这种验证能有效降低被判定为spam的几率
原来也是这么做的,但是奈何太麻烦,就放弃了,换用gmail
@kslr: 不习惯SMTP
从你的DNS解析中可以看到,你的DKIM是不完整的,DKIM说简单也简单,但要做好还是有点麻烦
SPF check: pass
DomainKeys check: pass
DKIM check: pass
Sender-ID check: pass
SpamAssassin check: ham
我的算是做得很完整了!
@今夜无眠: 你在哪里测试的呢?或许可以指教指教?
你在哪里测试的呢?或许可以指教指教?
@kn007:
加我QQ:83922808
这个过程有点复杂,而且也不知道你主要是发哪些邮件
测试过程的话有二种
check-auth-97500391=qq.com@verifier.port25.com
check-auth-sogouwz=163.com@verifier.port25.com
能看得懂吧?
所回复邮件地址修改下即可,97500391 sogouwz修改成你的,你就能收到回复了,要用你的服务器发送哟
第二种方法
http://www.mail-tester.com/
这里可以查看你的IP信誉,希望对你有帮助,呵呵
你这个DKIM按理是简单的验证,要达到我的效果还是需要在基础上学习下
没那么简单!
@今夜无眠: 嗯,我一会有时间试一试,谢谢。
另已加Q。
大神,你的DKIM彻底解决了吗?
@trier: 早解决了啊。不是还有后续文章么。
@kn007: 实在不好意思,没看完所有文章。
你这个系列文档总结的真的很棒!很受用!